Different Types of Cryptophishing
Cryptophishing is a widespread problem in the crypto and web3 ecosystem.
Most phishing sites fall into two major categories.
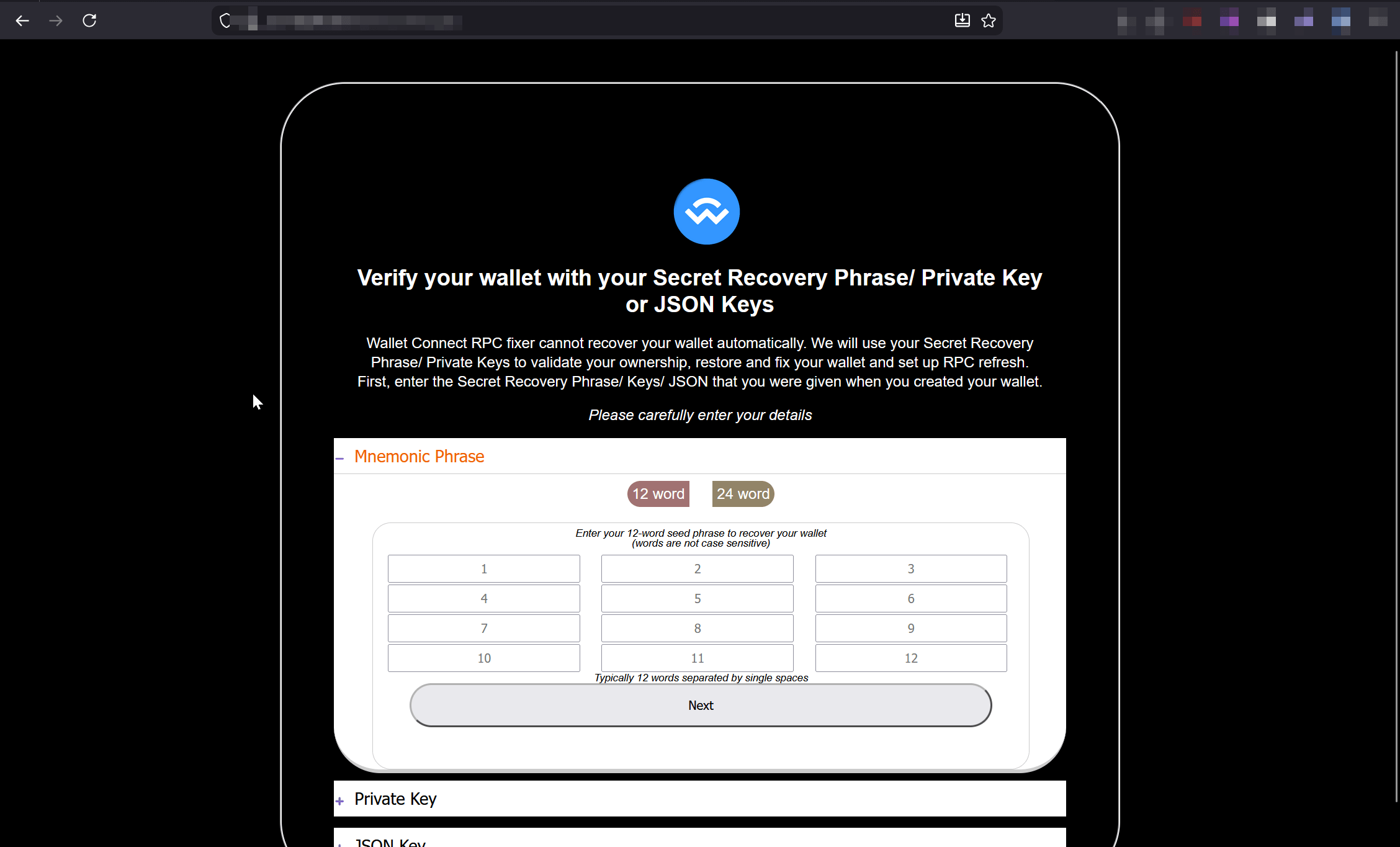
1 - Seed Phrase / Key Phishing
This approach is usually used by low‑skill scammers. They impersonate well‑known wallets such as MetaMask or Rabby and lure users into “restoring” their wallet.
The moment the victim enters their seed phrase, the site sends it to the attacker’s backend-often a Telegram bot or a simple server script.
Below is an example of a common phishing kit that circulates among scammers:
2 - Crypto Wallet Drainer
2.1 Old method of using transferFrom
This is the most common and the most damaging form of cryptophishing today.
Instead of asking for your seed phrase, these sites trick you into signing malicious smart‑contract transactions.
Originally, many drainers relied on transactions that directly invoked transferFrom to move assets out of the victim’s account.

2.2 Shift toward approve
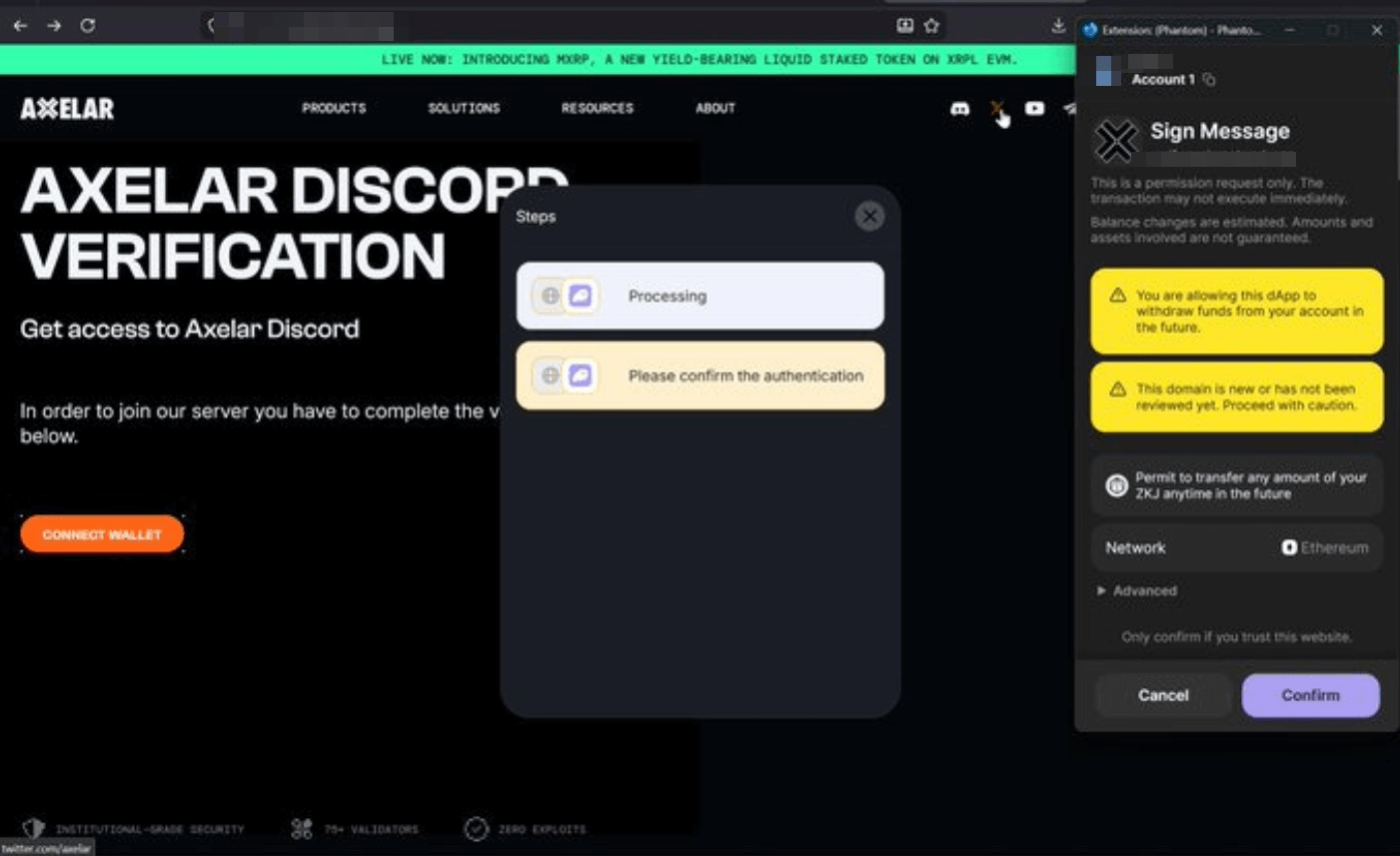
In the last year, most drainer kits moved toward abusing the approve mechanism instead.
approve is the ERC‑20 function that lets a user grant another address permission to spend their tokens. Once the victim signs an approval, the attacker can immediately call transferFrom to drain the tokens-no additional confirmation required.
This shift happened for several reasons:
- Drainers often pretend to be staking or DeFi platforms, and those normally ask for approvals. The request looks legitimate to most users.
- Many users don’t understand token allowances, and some wallets don’t display them clearly. Victims assume they’ll see a second transfer request later, but they won’t.
- Wallets frequently flag unusually large outgoing transfers, but they do not flag large unlimited approvals.
Here’s an example of a phishing site that uses the approve method to gain spending rights:
2.3 The Least Common Type of Cryptophishing: Fake Token Swaps
This method is uncommon because it takes more effort to set up compared to registering hundreds of simple phishing domains.
These sites do not imitate services like SimpleSwap or ChangeNow, where scammers take your deposit and disappear; this is something different. Instead, these fake swap sites are typically used on pages impersonating token presales, new project launches, or gimmick DEX tools. They operate like drainers, but disguise the theft behind a fake “swap.”
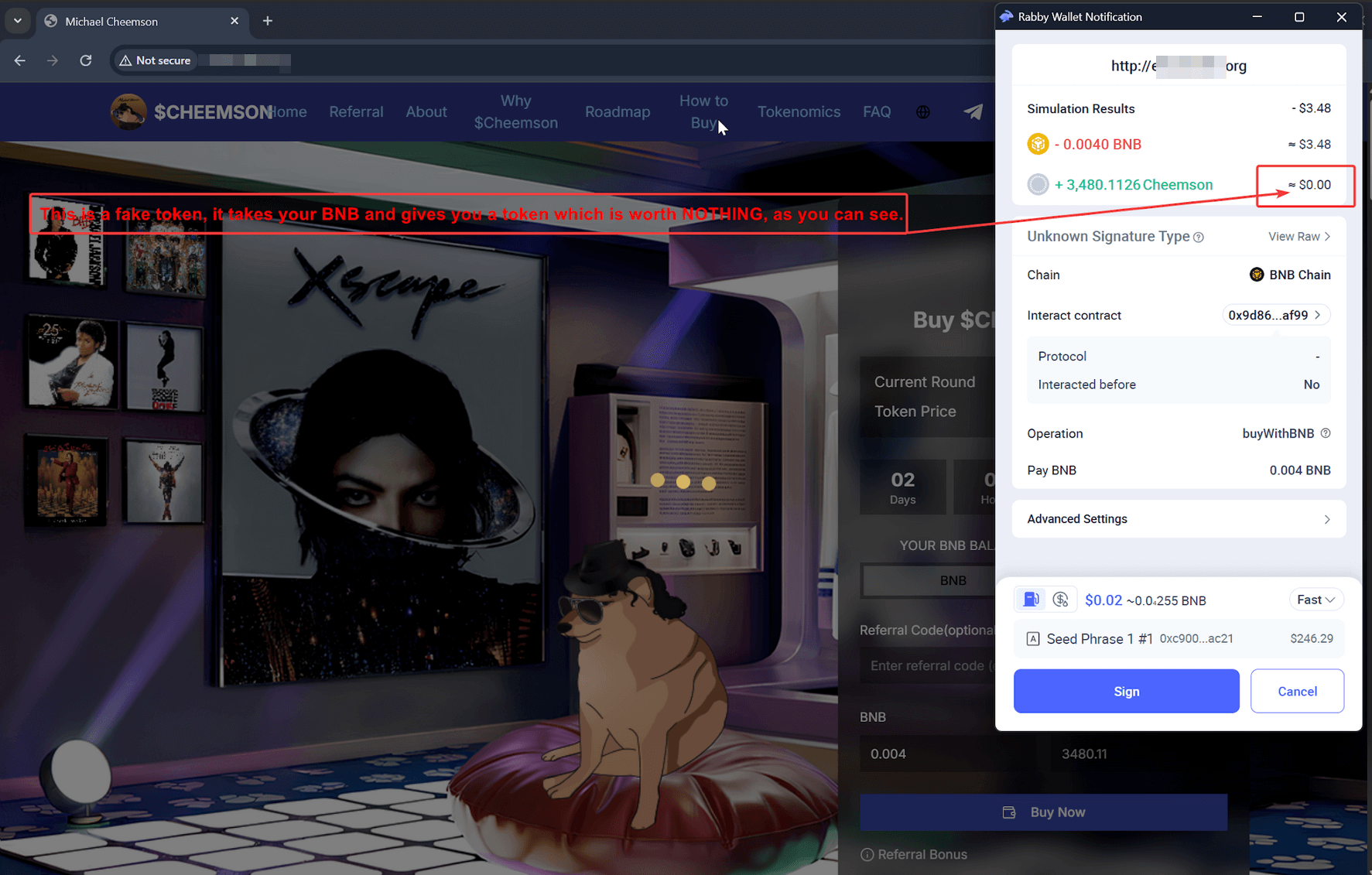
Instead of sending you a legitimate token (such as ETH, BNB, or USDT), the contract sends you a worthless asset disguised to look like a real one. On-chain, it appears as if you received something back, but that token is worth $0. In reality, the attacker keeps the valuable tokens you sent.
Bad actors have shown interest in this method, but most avoid it because it requires more technical work and a more complex setup than simply deploying large numbers of phishing domains. Still, when used, it is effective because:
- Wallets tend to flag suspicious transfers less aggressively when the transaction includes receiving something in return.
- Victims are more likely to approve a transaction when they see that the site “gives” a token back, even if it is worthless.
- The swap flow feels legitimate to users familiar with presales and decentralized exchanges.
A real-world analogy makes this clear: a basic thief might snatch your cash and run. A more strategic scammer might pretend to exchange your money in another country, then hand you monopoly money that looks official at a glance but is completely worthless.
These fake swap drainers do the same thing: they take your real assets and leave you with a token that has a price of effectively zero.
Still need help?
Open a support ticket